how to use Cipher Suite shell script based encryption decryption application
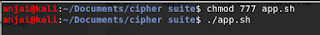
we should give execute permission to shell script file before use shell script on my computer. so blow image shows how to provide execute permission for the user. and also, it contains execute the command after execute the app.sh terminal will show the welcome interface. that interface contains symmetric encryption, asymmetric encryption, and exit part. If i choose symmetric encryption technique system will ask for the operation. when i will choose encryption part system provides encryption algorithms information so we may select one of the above algorithms. after this system ask encryption key from the user. if a user provides the password, the system shows the status and store the encrypted file into the computer. likewise, decryption functions also will happen. Note we must use the same key for encryption and decryption. if you choose asymmetric encryption system will ask same questions but the last question is different(system ask to choose key option). i choose